Passkeys: The Future of Login Security
An Introduction to the Future of Authentication
Have you ever reinstalled your favorite app on a brand-new device, only to be greeted by a screen asking you to type in your credentials like it’s still the Stone Age? And you thought: There has to be a better way! Well, now there is. Finally, authentication has entered the 21st century, and you no longer need to rely on that one password you use for 30 other services (please don’t do this), or hunt through your password manager because the integration didn’t work, and your credentials weren’t auto-filled.
Now, you can simply tap your finger on the scanner or make a face at the camera, and it’s done!
In recent years, you’ve probably noticed the growing trend of passkey authentication with major services like LinkedIn, GitHub, and Amazon.
What Are Passkeys?
According to Verizon’s Data Breach Report, 81% of hacking-related breaches are caused by weak or stolen passwords, and malicious phishing emails have skyrocketed by a staggering 1,265% since Q4 2022, as reported in the SlashNext 2023 State of Phishing Report.
The FIDO Alliance—FIDO stands for "Fast IDentity Online—" is the group that has taken it upon itself to tackle these problems.
The origins of this initiative trace back to 2009 when PayPal and Validity Sensors began discussing the use of biometric sensors for online user identification instead of passwords. Fast forward to 2012, the FIDO Alliance was founded by PayPal, Lenovo, Nok Nok Labs, Validity Sensors, Infineon, and Agnitio. [Source]
Today, the alliance’s members include major companies like Google, Microsoft, Apple, Intel, Amazon, TikTok, American Express, Lenovo, Samsung, Qualcomm, Visa, and many others.
Over the years, FIDO has developed numerous standards. In 2016, the W3C launched a new effort to create a web authentication standard based on FIDO’s FIDO2 2.0 Web API specification.
By 2018, the W3C Web Authentication standard reached candidate recommendation status, and FIDO2 was officially launched. Major web browsers adopted these standards, including Chrome, Mozilla Firefox, and Microsoft Edge.
In 2019, WebAuthn became an official web standard, and Android and Windows 10 earned FIDO2 certification the same year. Apple, as usual, was late to the party, joining in 2020 with FIDO2 certification for its products. [Source]
Passkeys, based on FIDO standards, are a secure and phishing-resistant replacement for passwords, allowing users to register and sign in to websites safely. [Source]
How Do Passkeys Work?
During registration with an online service, the user’s device creates a cryptographic key pair—Passkeys—using standard public key cryptographic techniques, which are bound to the web service’s domain. The public key is sent to the web service for registration, while the private key remains stored securely on the device. [Source]
Register Using a Passkey
The client requests a random challenge from the server.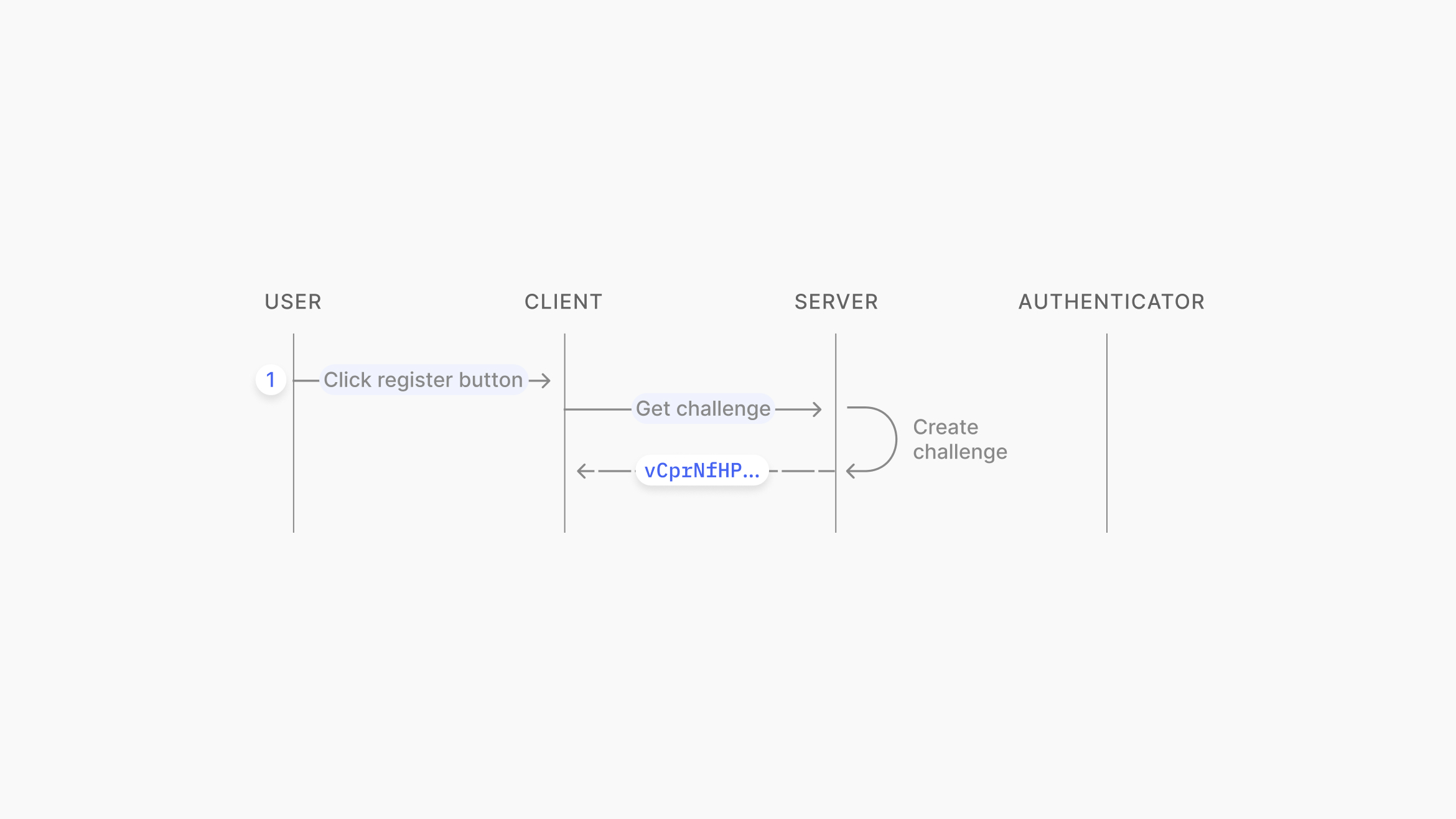
Source: https://www.passkeys.io/technical-details#passkeys-under-the-hood
On the client side, the WebAuthn API is called with credentials.create(challenge), which generates the key pair on the device. In WebAuthn terminology, this device is called an "Authenticator." The challenge is signed using the private key (passkey) and is stored on the user’s device inside secure storage (TPM or secure enclave). Verification may be required using biometrics or a PIN code.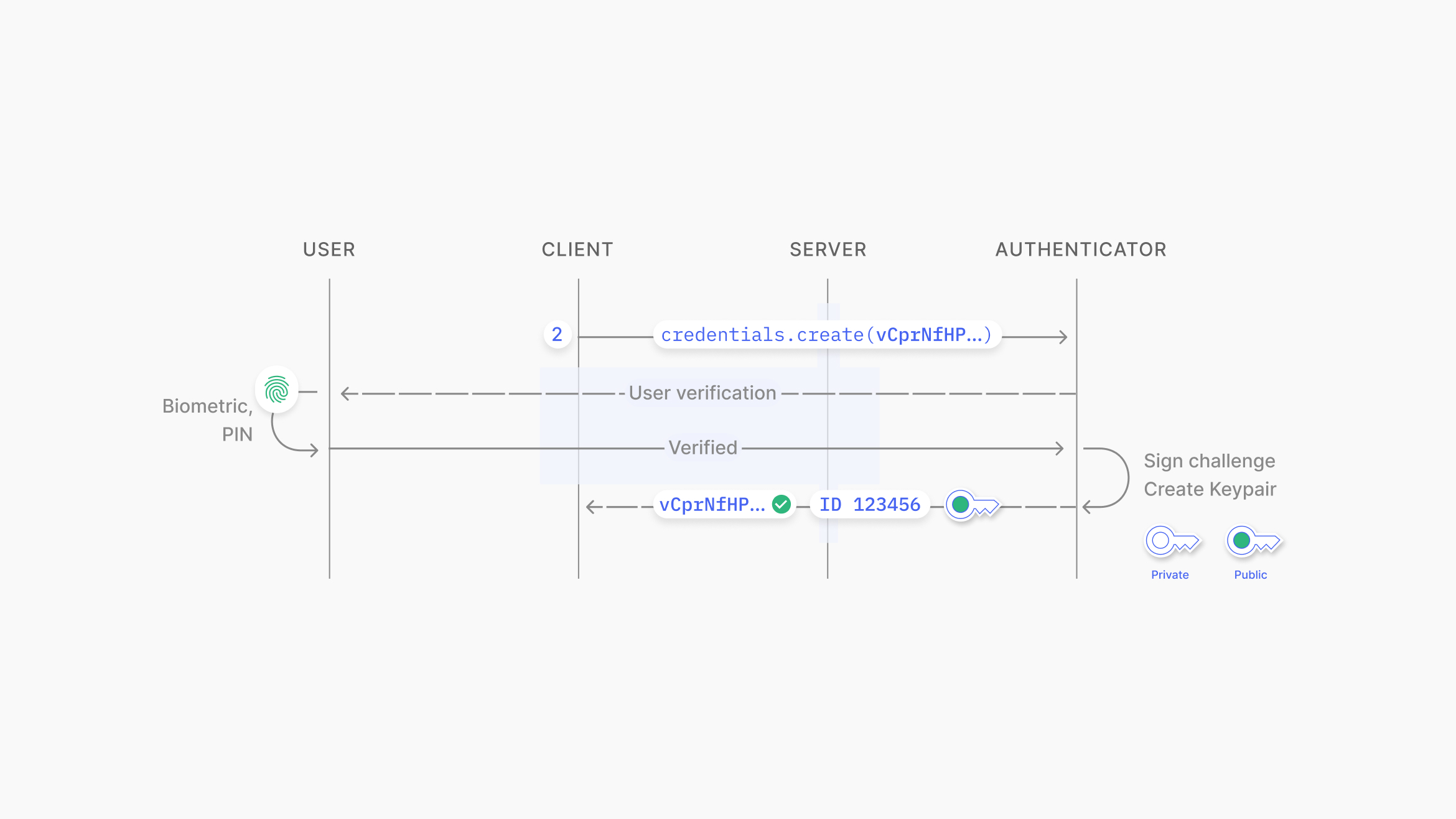
Source: https://www.passkeys.io/technical-details#passkeys-under-the-hood
To complete registration, the public key, credential ID, and signed challenge are sent to the server. The server verifies the challenge’s signature using the public key and associates the public key and credential ID with the user for future authentication.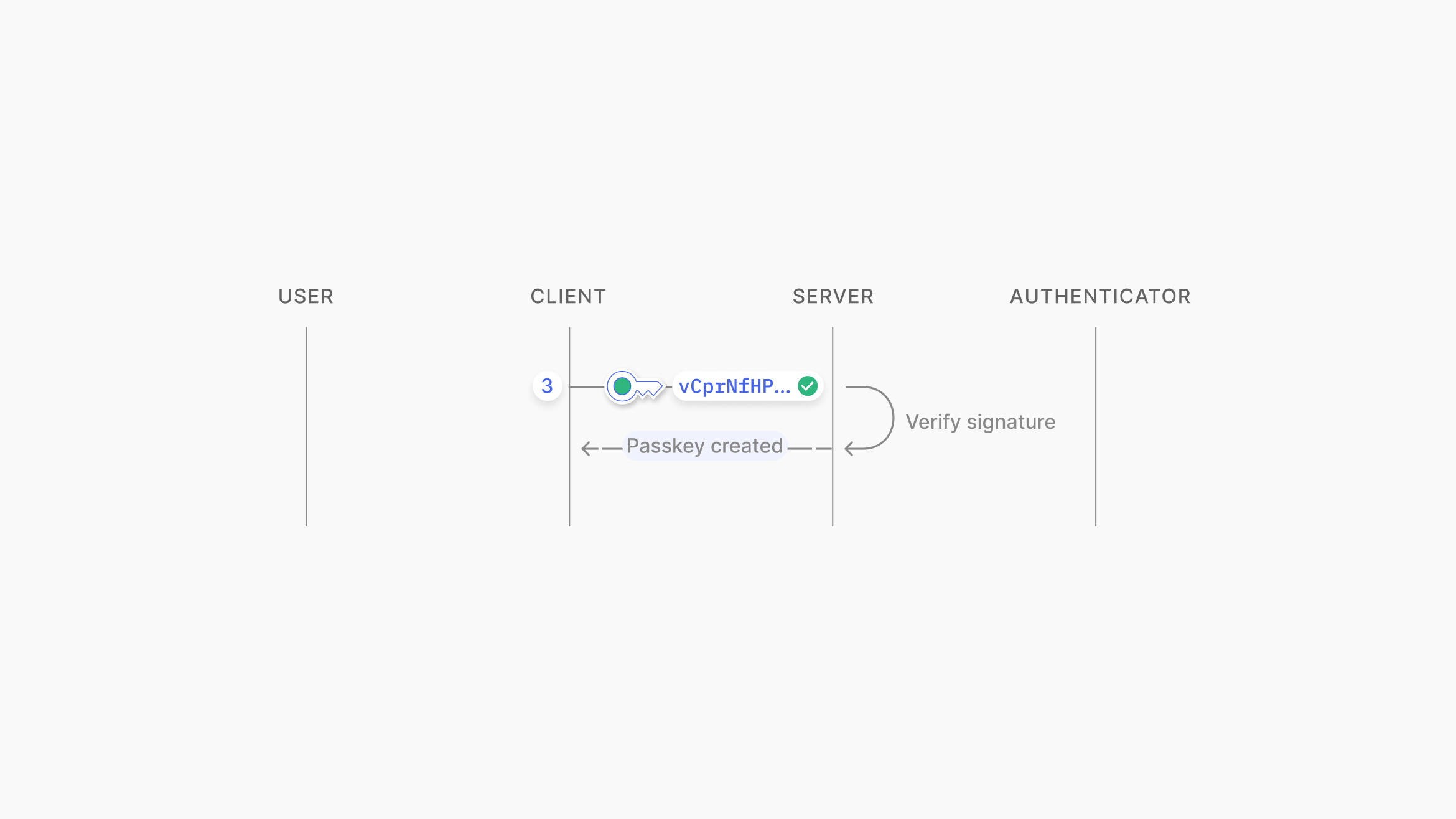
Source: https://www.passkeys.io/technical-details#passkeys-under-the-hood
Authentication Using Passkeys
When signing in to a web service, a random challenge is requested from the server.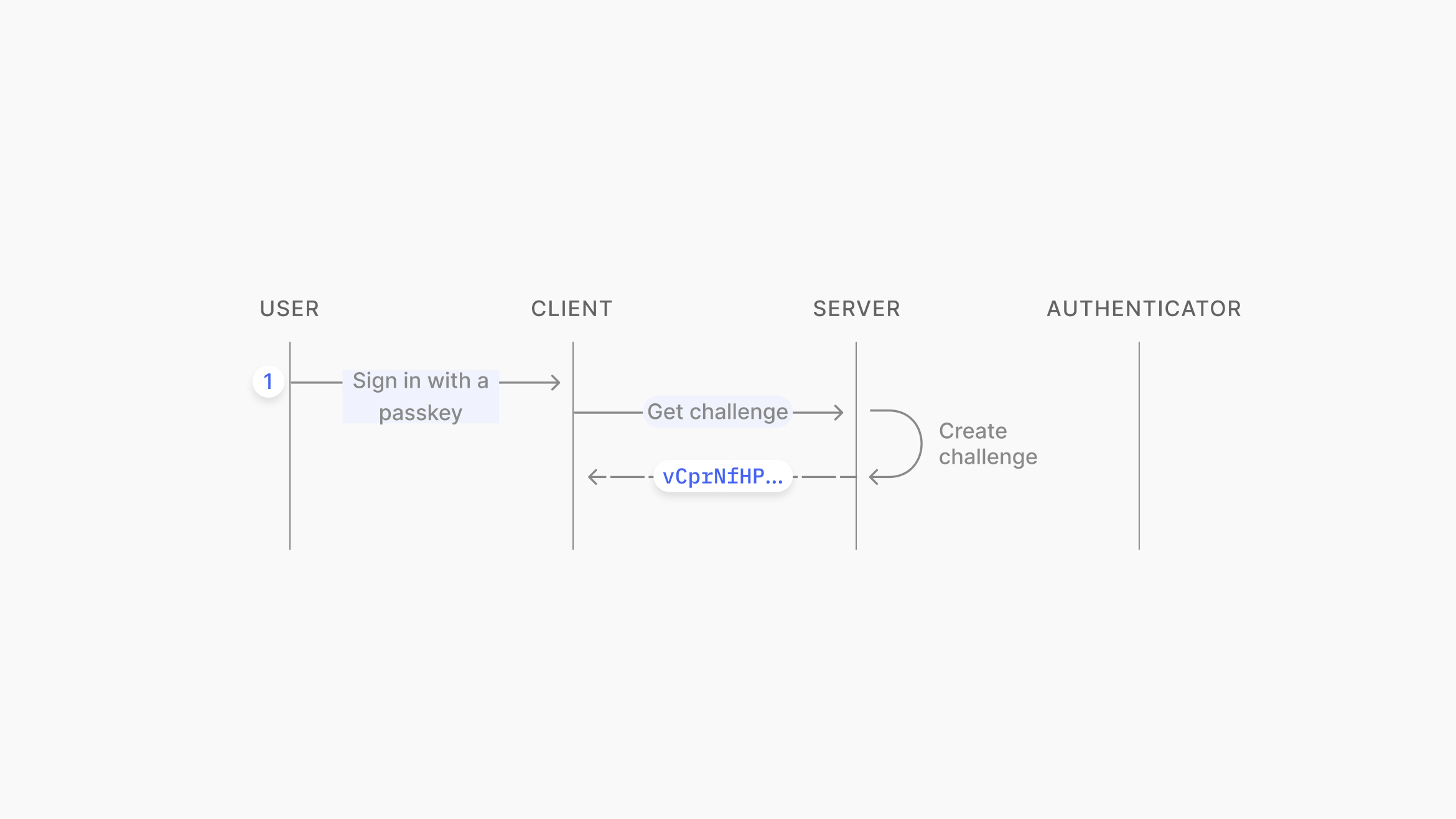
Source: https://www.passkeys.io/technical-details#passkeys-under-the-hood
On the client side, the WebAuthn API is called with credentials.get(challenge). The user is prompted for verification via biometrics or a PIN, and the challenge is signed using the private key stored on the device, associated with the web service’s domain. This function returns the signed challenge and the credential ID.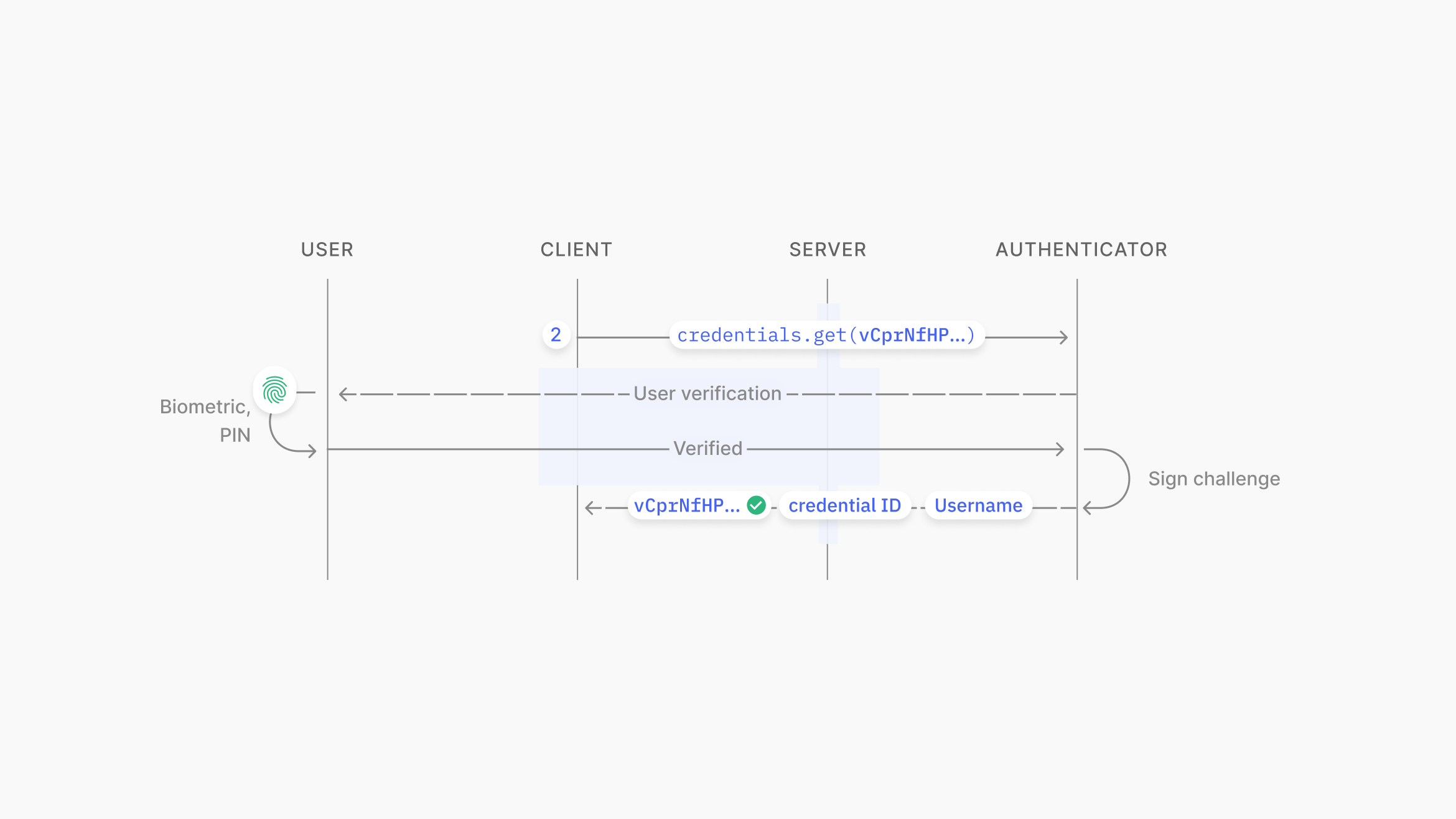
Source: https://www.passkeys.io/technical-details#passkeys-under-the-hood
To complete authentication with the web service, the signed challenge, username, and credential ID are sent to the server. The server verifies the signature using the public key associated with the credential ID and username.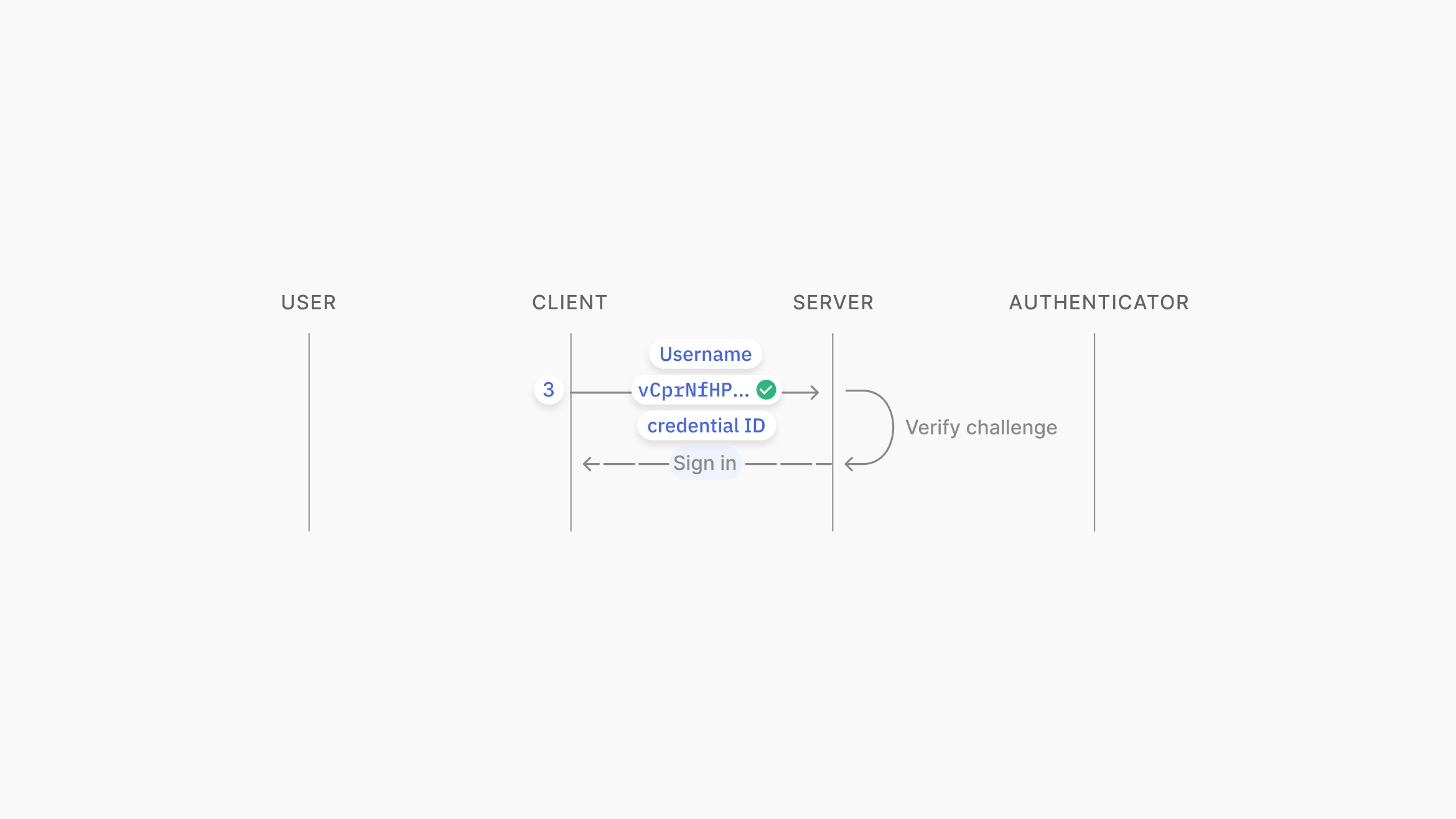
Source: https://www.passkeys.io/technical-details#passkeys-under-the-hood
Device Support
At the time of writing, all major web browsers support Passkey authentication. Specifically, Chrome supports it from version 108, Firefox from version 122, and Edge from version 122.
Thanks to FIDO’s Cross-Device Authentication (CDA), passkeys created on mobile devices can also be used on desktop operating systems. Support for the CDA Client was added in the following versions: Windows 11 23H2, macOS 13, and Chrome OS 108. The exception is Ubuntu, which supports the CDA Client only via Chrome or Edge.
More information about the current state of support for operating systems and browsers can be found here.
You can test if your device supports Passkeys by visiting https://webauthn.io.
Passkeys in the Android Ecosystem
Android offers deep integration with Passkeys via Google Password Manager, included as part of the Google Play Services package. When users select Google Password Manager as their passkey provider, their passkeys are automatically synchronized across all devices linked to their Google account. [Source]
Starting with Android 14, users can choose third-party passkey providers on their devices. This new API allows third-party apps to register as passkey providers, enabling users to choose their preferred passkey manager (such as 1Password, Dashlane, or other supported services) for storing and using passkeys across apps and websites. [Source]
Passkeys are securely stored via the Credentials Manager API, which supports various credential types, including passwords, OAuth tokens, and passkeys. These passkeys are stored in a dedicated hardware component called the Trusted Execution Environment (TEE), which operates independently from the main Android operating system. This isolation ensures that even if an attacker gains root access to the device, they cannot directly interact with or extract data from the secure environment. [Source]
Passkeys in the iOS/Apple Ecosystem
Apple provides deep integration with passkeys through the native Passwords app (since iOS 18) or via the Settings app in previous versions. Users' passkeys are automatically synced across all devices linked to their Apple ID. [Source]
Starting with iOS 17 and macOS 14, users can choose third-party passkey providers on their devices. Similar to Android, the new APIs allow third-party apps to register as passkey providers.
Users can create groups to share passwords and passkeys, share a passkey via AirDrop, or log in on a different device with a passkey from their device using a QR code for the connection. Like passwords, passkeys are encrypted and stored in the user’s iCloud Keychain, where they remain invisible to everyone, including Apple. [Source]
Conclusion
Passkeys are a big leap in security and authorization, and based on widespread usage, they are here to stay. Major OS players are finding ways to support them, allowing users to authorize more securely and comfortably. It seems it’s only a matter of time before passkeys become the preferred option for user authorization. What a time to be alive!



